Server Preparation for Compliance¶
Windows 10¶
Running OpenSCAP
The OpenSCAP scanner requires Microsoft Visual C++ Redistributable to be installed.
Configuring WinRM over HTTP¶
To enable access via HTTP, follow these steps:
-
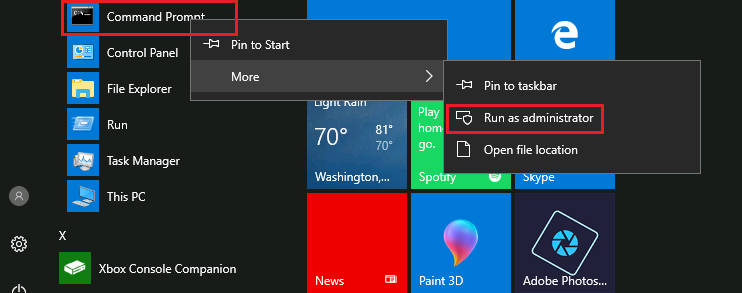
Run Command Prompt as Administrator:
-
Run the
winrm qccommand: -
If the command fails (as shown below), ensure that your network is set to
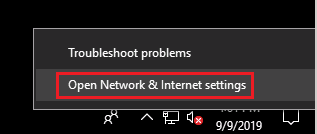
Private / Domain:- Click the network icon in the bottom-right corner of the screen, then select
Open Network & Internet Settings:
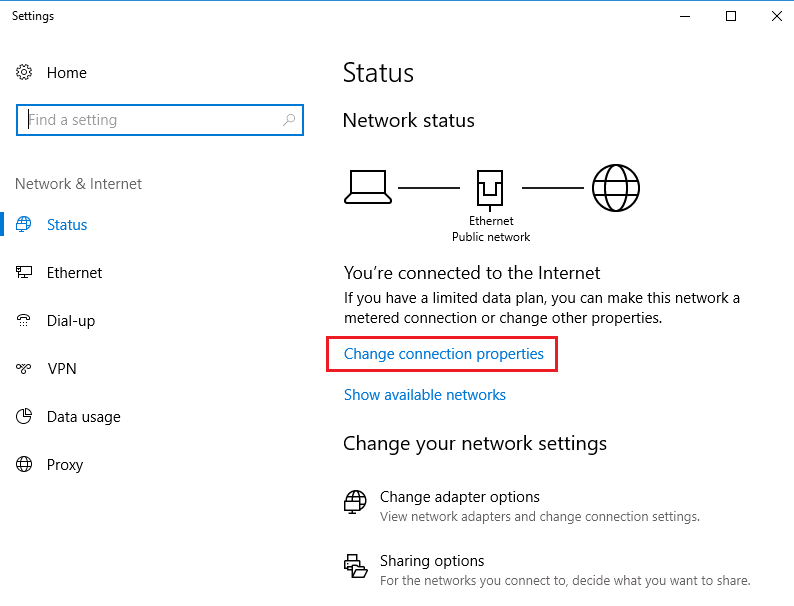
- Switch the network type to
PrivateinChange connection properties:
- Click the network icon in the bottom-right corner of the screen, then select
Configuring WinRM over HTTPS¶
To enable access via HTTPS, first complete the steps for HTTP, then run the following commands in PowerShell as Administrator:
$ip="192.168.137.169" # your ip might be different
$c = New-SelfSignedCertificate -DnsName $ip `
-CertStoreLocation cert:\LocalMachine\My
winrm create winrm/config/Listener?Address=*+Transport=HTTPS "@{Hostname=`"$ip`";CertificateThumbprint=`"$($c.ThumbPrint)`"}"
netsh advfirewall firewall add rule name="WinRM-HTTPS" dir=in localport=5986 protocol=TCP action=allow
Windows Server¶
Running OpenSCAP
The OpenSCAP scanner requires Microsoft Visual C++ Redistributable to be installed.
WinRM Protocol is enabled by default on Windows Servers, but you need to update rule in firewall:
- Open
Inbound Rulesin theWindows Firewall. - Locate the rule
Windows Remote Management (HTTP-In). - In the
Scopetab, underRemote IP Address, selectAny IP address.
HTTPS access for Windows Server
To configure HTTPS access, follow the same steps as for Windows 10.
Linux¶
To add a Linux server, you can use one of two SSH authentication methods:
- Password-based authentication
- SSH key-based authentication
Password-Based SSH Authentication¶
To enable password-based access, enter a valid password in the Password field.
SSH Key-Based Authentication¶
To add access using an SSH key, you must perform the following steps:
-
Connect to the server and open a
Terminal. -
Generate a key pair using the command:
-
Enter the command:
-
Add the public key to the
authorized_keysfile:cat /tmp/compliance_key.pub >> ~/.ssh/authorized_keys -
Copy the private key using the
cat /tmp/compliance_keycommand and paste when connecting the server to Compliance.