VPN Gateway¶
VPN Gateway is a network service that provides a secure virtual private network (VPN).
The primary goal of the service is to provide users and developers with an easy and secure way to access their cloud account resources through a VPN.
When you create an account, a multifunctional Cloud Gateway virtual machine is automatically created, which plays the role of a VPN server (or VPN gateway). To connect to the VPN service, the device must have a Wireguard client.
VPN Gateway functionality:
- creating VPN connections and adding VPN client devices;
Remote Gatewayallows you to combine account networks in different locations if the client uses the ICDC Platform in several regions;NAT Mapping- IP address translation to solve subnet crossing problems.
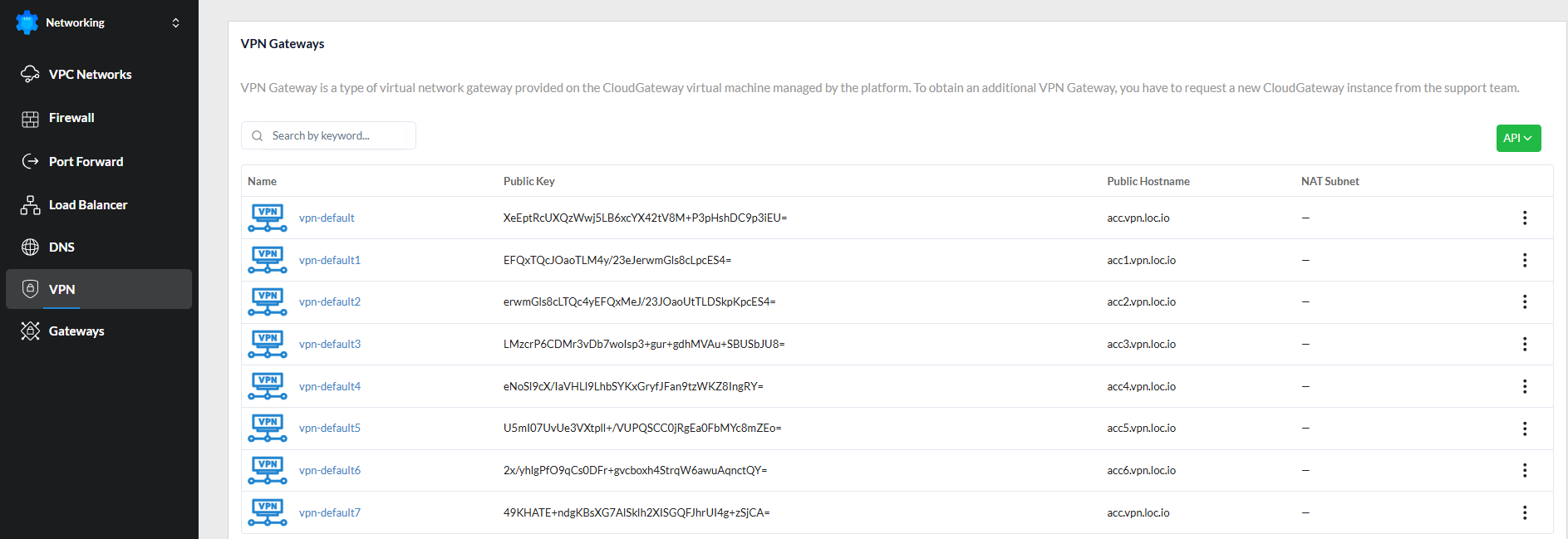
VPN Gateways¶
The VPN tab displays a list of VPN Gateways.
A VPN Gateway is a type of virtual network gateway that is provided on top of a CloudGateway virtual machine that is managed by the platform.
The VPN Gateway has a public Wireguard key that is used for all connections. Each VPN Gateway has its own Public address, and by default, the first Gateway receives the Public Hostname - account_name.vpn.location_name.icdc.io.
Here you can also set the NAT Subnet - this is an additional subnet that does not exist in the location and on user devices, for the IP-addresses of which its addresses are translated into the internal IP addresses of virtual machines.
This allows you to bypass the problem of crossing IP ranges on client devices and account networks.
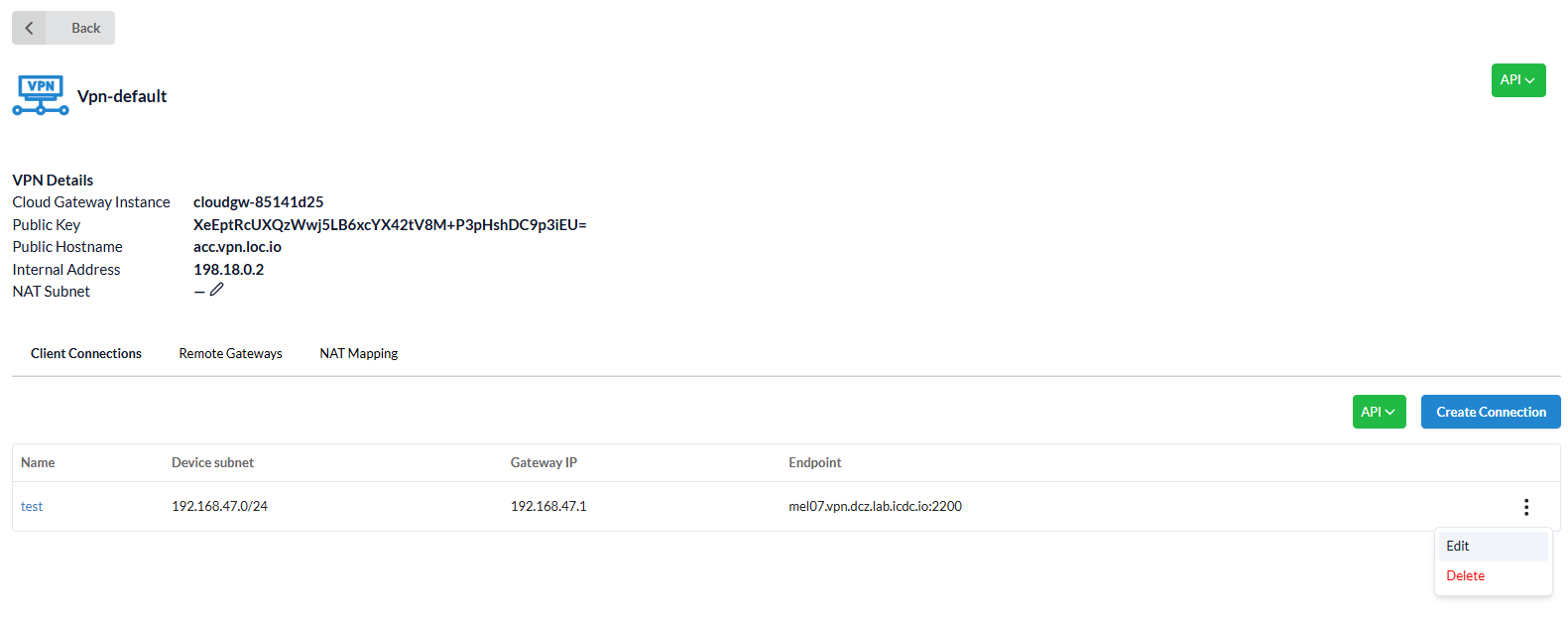
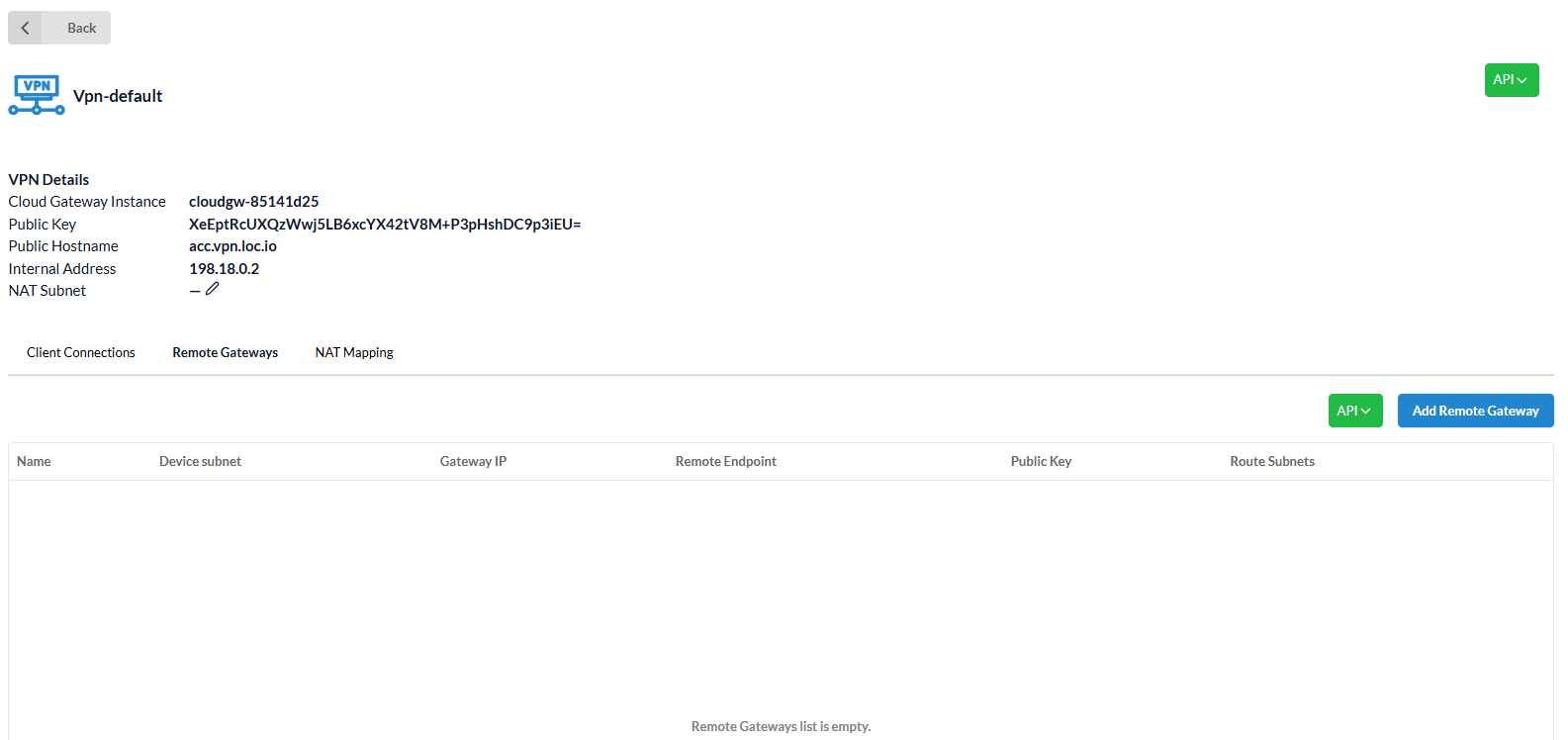
Users can view the VPN Gateway Details by opening it from the list.
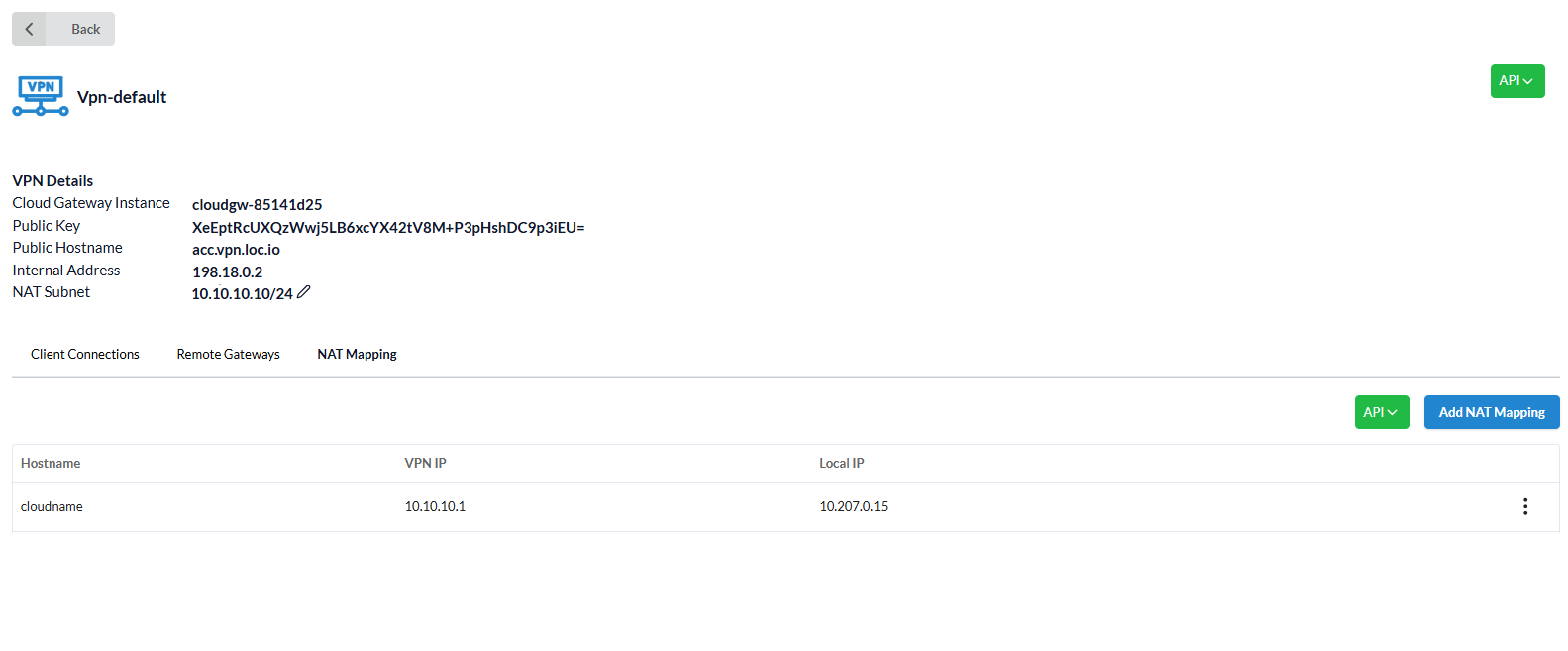
VPN Details specify:
Cloud Gateway Instance- indicates the instance in which the Gateway is running;Public key- public Wireguard key;Public Hostname-account_name.vpn.location_name.icdc.io;Internal address- Cloud Gateway address in the internal infrastructure, needed to configure internal routes. (For example, if you need to send traffic to another location through Cloud Gateway, then you need to know the internal IP address of the Gateway);NAT Subnet- an additional subnet whose IP addresses are translated into internal IP addresses of virtual machines. (optional)
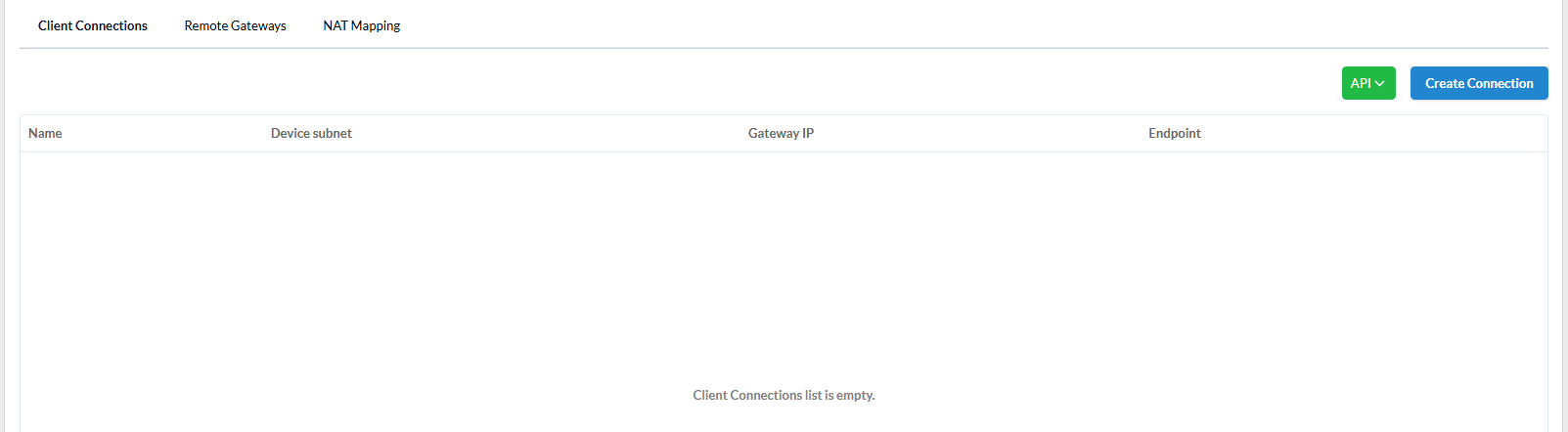
Client Connections¶
The user can define one or more client connections (for example, for different user groups).
In the client connection, the user must specify the Device subnet (and VPN Gateway IP address within it) that will be used to allocate IP addresses to client devices. This subnet must not intersect with existing VPC networks and subnets on client devices.
New route creation
Also, in the VPC Networks application, in the Routing tab, the user needs to add a new route (use Create button) to the selected subnet through the internal address of the VPN Gateway (usually 198.18.0.2).
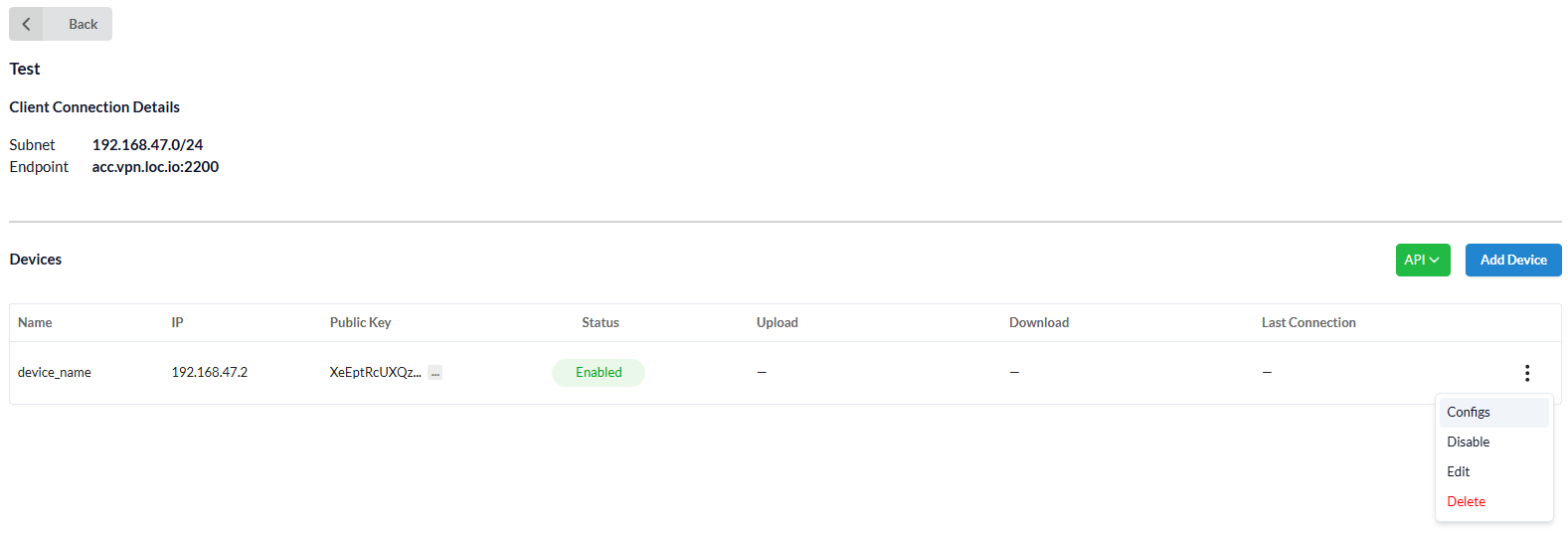
The Client Connections tab displays:
Name of connection- used to generate the name of the VPN and NIC network connections on the client device;Device subnet- range of IP addresses from which IP addresses will be allocated to devices;Gateway IP- Gateway IP address;Endpoint- public Endpoint to which the connection is made.
IP Masquerading in VPN
To simplify access to VMs within the VPN, the IP addresses of VPN clients are masqueraded by default. This means the source IP address of the VPN client device is replaced with the IP address of the VPN Gateway (usually 198.18.0.2).
As a result, all clients have the same IP address when accessing applications running on VMs.
Router as VPN client
To simplify access from VMs to VPN client-side networks, when the client device is a router that provides access to client-side networks, the IP addresses of VMs are masqueraded by default (source NAT is configured). This eliminates the need to configure routes on the client's router.
However, as a downside, the source IP address for all VMs seen on client-side systems will be the same (the IP address of the VPN Gateway).
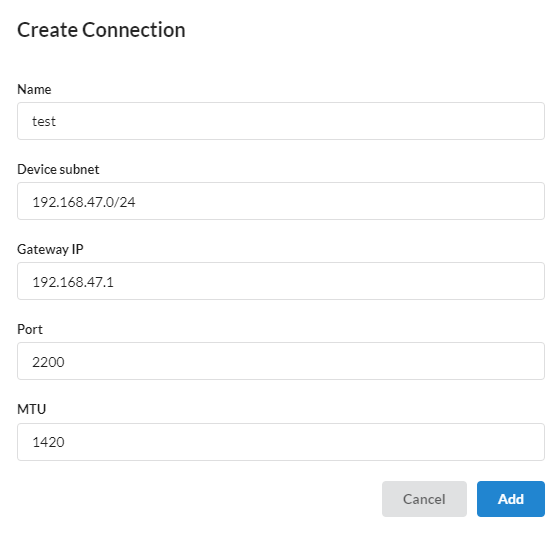
Connection creating¶
Users can create a connection by clicking the corresponding button - Create Connection.
To create a connection, you need to specify:
Nameof connection;Device subnet- IP address of VPN Gateway on client connection subnet;
Important
The Device Subnet must not overlap with other subnets within the same account that are defined in VPC Networks.
Gateway IP- Gateway IP address;Port- UDP port on the public IP address;
Recommendation
We recommend using port 2200/udp for the first connection, as it is pre-configured and intended for VPN connections. For subsequent connections within the account, please contact Support for port configuration assistance.
MTU- maximum transmission unit, the recommended value -1420;Enable NAT for the subnet- this option simplifies network configuration by enabling network address translation (NAT) for all VPN devices. It eliminates the need to configure network routes and security groups to access target VMs.
Click Add.
The created connection will be displayed in the Client Connections tab, and it can be modified or deleted using the sidebar menu.
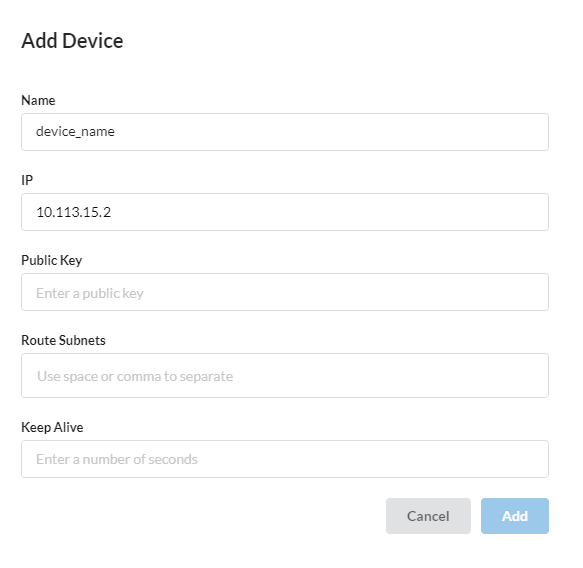
Device adding¶
Clicking on the name of a Client connection takes the user to a Client Connection Details page where they can add device(s) to the client connection by clicking on the Add Device button.
To add a device, you need to specify:
Nameof device, e.g.John-laptop,Maria-phone;IP-addressof the device, which is generated based on the IP address of the subnet of the client connection;Public key- public key that is generated on the device when creating a new connection in the Wireguard software;Route Subnets(optional) - only used if the device is a remote location VPN gateway.
Here you specify the subnets that need to be routed from a remote location so that traffic from remote networks reaches the networks of the current account;Keep Alive(optional) - time interval during which a packet is sent to maintain a connection to the device's UDP port.
The network firewall behind which the user device is located closes unused connections after a certain interval (usually 30 seconds). Therefore, the common value is 25 seconds.
Click Add.
The added device will appear in the Device list. The added device will appear in the device list, where the sidebar menu allows for modifying the configuration, updating the entered data, disabling, or deleting the device.
Remote Gateways¶
Information on remote gateway can be found in the Remote Gateways tab:
Name- name of the gateway;Device subnet- range of IP addresses from which IP addresses will be allocated to devices;Gateway IP- IP address of the gateway;Remote Endpoint- public Endpoint to which the connection is made;Public Key- Wireguard public key;Route Subnets- subnets that need to be routed from a remote location so that traffic from remote networks reaches the current account.
Route Configuration¶
Adding a remote gateway allows to quickly integrate account networks located in different remote locations. It can also be used to connect the account's networks to a remote Wireguard VPN server, for example, installed in the customer's branch office.
To create network visibility in two different locations (for example, loc1 and loc2), you need to configure static routing:
-
add routing in
loc1location:- Go to VPC Networks page, select the
Routestab and configureRoute subnetson subnets fromloc2; - Go to the VPN page, select Gateway, and then select the
Remote Gatewaystab and configureRoute subnetson subnets fromloc2.
- Go to VPC Networks page, select the
-
add routing in
loc2location:- Go to VPC Networks page, select the
Routestab and configureRoute subnetson subnets fromloc1; - Go to the VPN page, select Gateway, and then select the
Client Connectionstab in the requiredDeviceconfigureRoute subnetson subnets fromloc1.
- Go to VPC Networks page, select the
Remote Gateway adding¶
Users can add a remote gateway by clicking the corresponding button - Add Remote Gateway.
To add a remote gateway, fill in the required fields and click Add.
The created remote gateway will be displayed in the corresponding tab.
NAT Mapping¶
Network Address Translation (NAT) allows replacing IP addresses from a free IP range of a NAT subnet to the IP address of virtual machines located in non-routable cloud subnets of an account. This may be needed if the client device already has overlapping IP address ranges.
For each NAT mapping, DNS records of the following type are also automatically created:
<hostname>.<acc>.vpn.<loc>.icdc.io
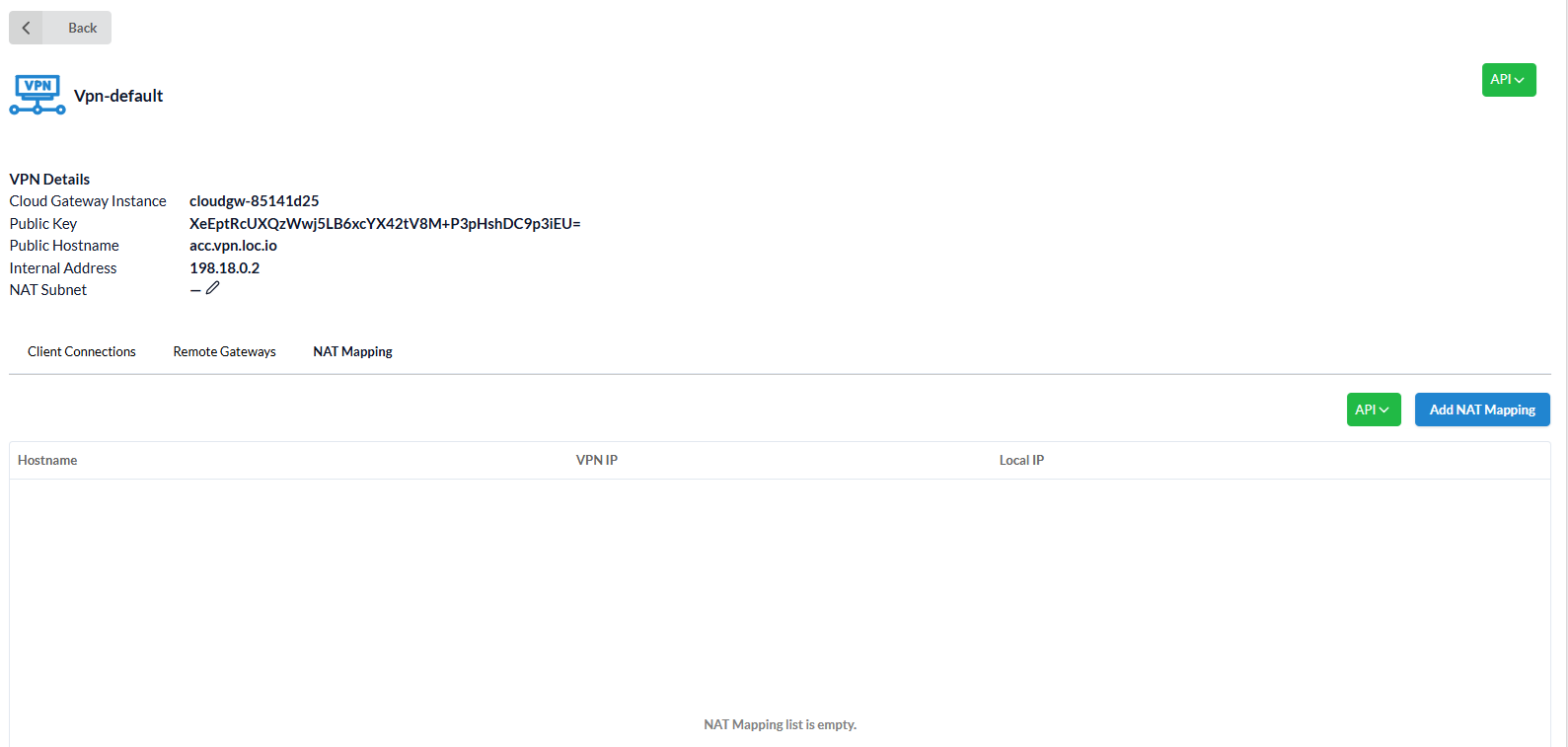
The NAT Mapping tab displays a list of added NAT mappings.
Each mapping contains:
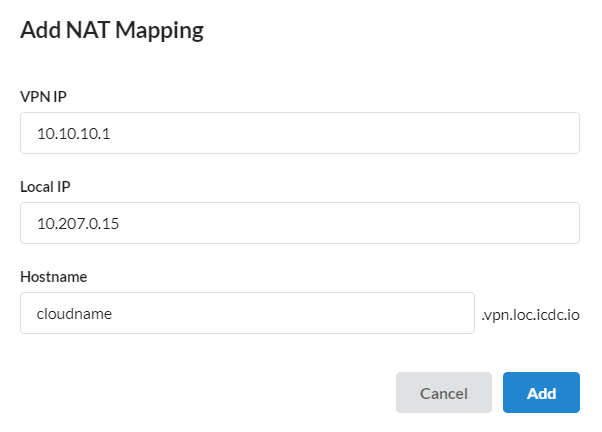
Hostname- automatically highlighted -account_name.loc.icdc.io;VPN IP;Local IP- any internal ip-address within the location.
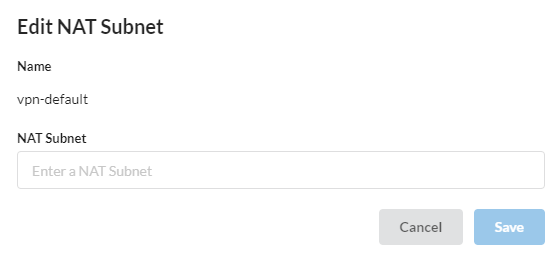
User can add/edit NAT Subnet using the edit button in VPN Details.
To make changes, the user needs to enter new data and click the Save or Cancel button - in case of canceling the changes.
To add a NAT mapping, click on Add NAT Mapping, enter the required information in the modal window, and click the Add button.
The added NAT will be displayed in the NAT Mapping tab:
Roles and permissions¶
| Action | Member | Admin | Owner | Operator |
|---|---|---|---|---|
| Create Connection | ✔ | ✔ | ✔ | |
| Edit Connection | ✔ | ✔ | ✔ | |
| Delete Connection | ✔ | ✔ | ✔ | |
| Add Device | ✔ | ✔ | ✔ | ✔ |
| Edit Device | ✔ only own | ✔ | ✔ | ✔ |
| Disable Device | ✔ only own | ✔ | ✔ | ✔ |
| Delete Device | ✔ only own | ✔ | ✔ | ✔ |
| Configs for Devices | ✔ only own | ✔ | ✔ | ✔ |
| Add Remote Gateway | ✔ | ✔ | ✔ | |
| Edit Remote Gateways | ✔ | ✔ | ✔ | |
| Delete Remote Gateways | ✔ | ✔ | ✔ | |
| Create NAT Mapping | ✔ | ✔ | ✔ | |
| Edit NAT Mapping | ✔ | ✔ | ✔ | |
| Delete NAT Mapping | ✔ | ✔ | ✔ |